Malicious actors are continually developing new ways to harvest lucrative credit card and personal information from transactions. It has never been more critical for merchants to follow security best practices.
There are specific steps you can take to clean you site, improve your security practices, and remove Google warnings from search results and browsers.
We strongly encourage you to implement these recommendations if your site has been affected by malware. You can also use them as a starting point for creating a comprehensive security plan to help prevent future attacks.
In most malware cases attackers are not developing new ways to penetrate Magento sites. Instead, they are taking advantage of existing, unpatched vulnerabilities, poor passwords, and weak ownership and permission settings in the file system – all things you can control!
To ensure the highest level of security, here are actions you can take to protect your business
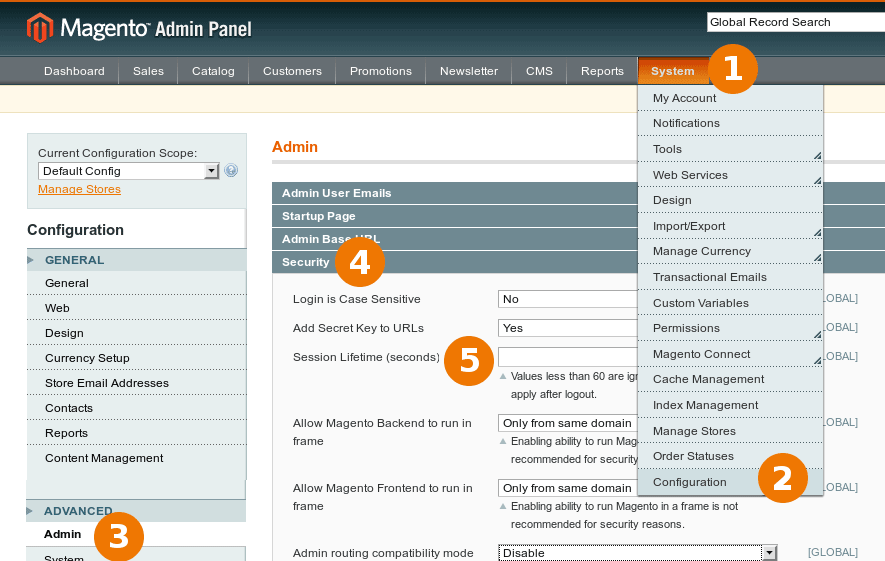
Set up strong passwords and change them at least every 90 days, as recommended by the PCI Data Security Standard in section 8.2.4. You can check your password lifetime setting in the following locations:
- Magento 2.x: Stores > Configuration > Advanced > Admin > Security > Password Lifetime set to 90 days (default setting)
- Magento 1.x: System > Configuration > Advanced > Admin > Security > Password Lifetime set to 90 days (default setting)
Keep your system up-to-date and install all patches and updates immediately.
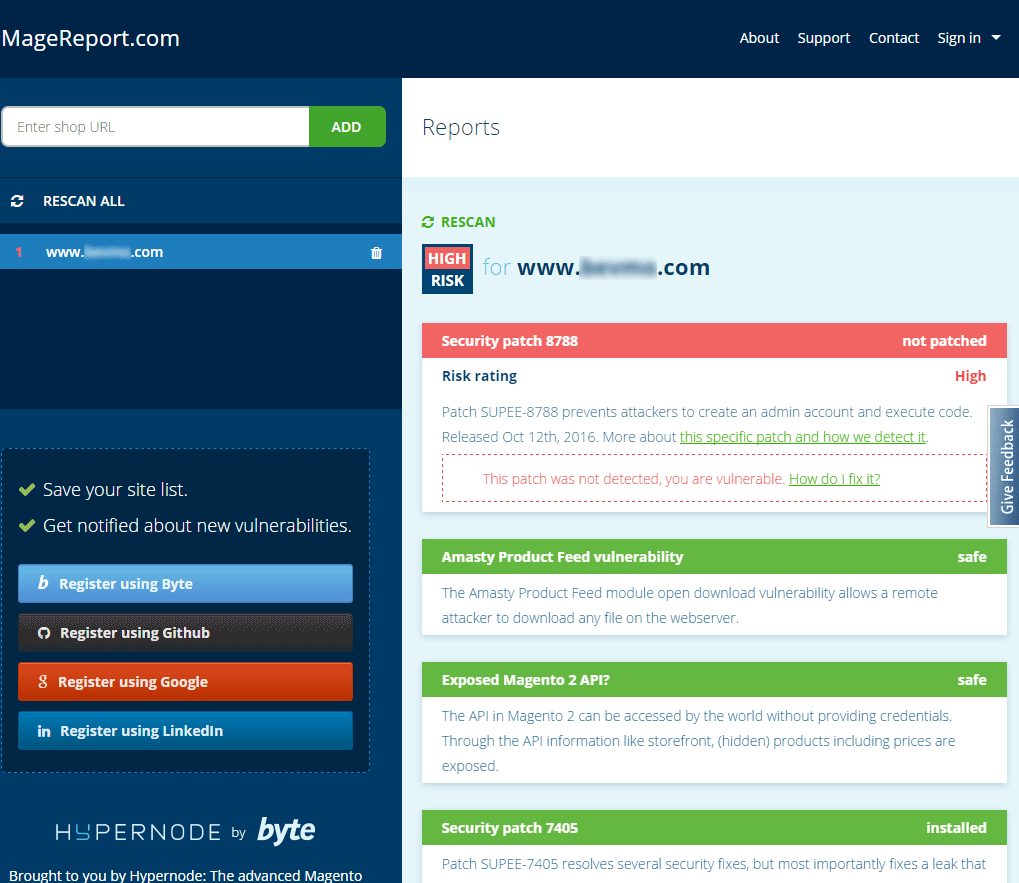
Scan your store monthly on MageReport.com to detect malware and to identify any security patches you may not have deployed. MageReport.com is a highly-regarded service that is available at no charge.
Remediating your site after a malware attack.
If you discover that your site has been attacked.
- Backup of your site’s data and files before making any changes.
- Scan your site on MageReport.com to identify any missing security patches and to determine if it has been infected with known malware strains.
- Install all missing patches and test store functionality in a non-production environment.
- Install the latest version of each Magento extension you use and test them in a non-production environment.
- Go to the Admin panel of your production site. Remove all unknown Admin accounts from System → Permissions → Users. Change passwords on all known Admin accounts and rename overly generic Admin usernames to an unique name
- Review all SSH and FTP users, remove old or unknown users, and change active users’ passwords.
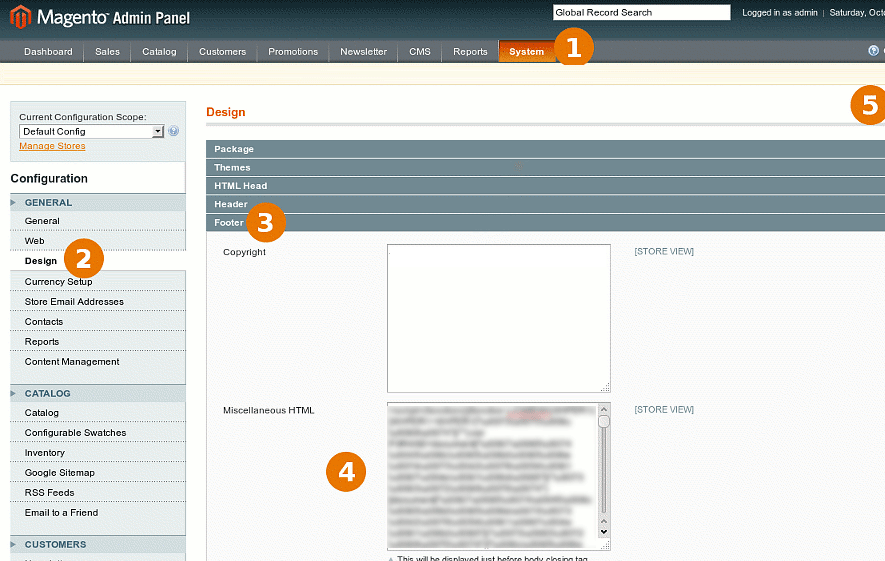
- Remove all unknown JavaScript code from System → Configuration → Design → HTML Head → Miscellaneous Scripts.
- Remove all JavaScript code from System → Configuration → Design → Footer → Miscellaneous HTML. Only put back code that you can recognize (e.g., tracking snippets).
- Verify the malware is no longer present by scanning your site with MageReport site.
- Make sure to secure your Admin panel by changing its front name and verifying that your site’s ‘app/etc/local.xml’ and ‘var’ urls are not publicly accessible in a web browser.
How to remove Google warnings
If your site has been flagged by Google as containing malicious code, you can request a review once your site has been cleaned. Reviews for sites infected with malware take a few days and once Google determines your site is clean, warnings from search results and browsers should be removed within 72 hours.
Information on how to request a review is available at https://developers.google.com/webmasters/hacked/docs/request_review.