Magento ecommerce platform is vulnerable to a zero-day remote code execution vulnerability, putting as many as 200,000 online retailers at risk.
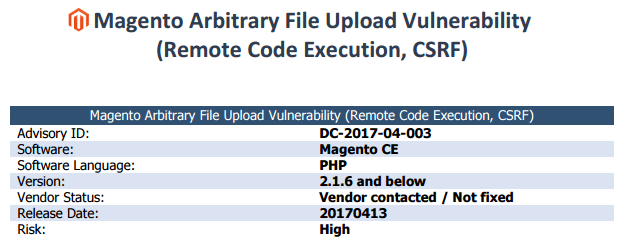
“During the security audit of Magento Community Edition, a high risk vulnerability was discovered that could lead to remote code execution and thus the complete system compromise including the database containing sensitive customer information such as stored credit card numbers and other payment information,” DefenseCode wrote in a technical description of its discovery Magento Arbitrary File Upload Vulnerability (Remote Code Execution, CSRF) .
Magento Security Team recommend
Magento is committed to delivering superior security to clients. Admin access is required to execute the exploit, so as always, we encourage you to follow best practices to keep your Admin secure.
This vulnerability will be addressed in next release of Magento. Until then, the Magento Security Team recommend enforcing the use of “Add Secret Key to URLs” to mitigate potential attacks. To turn on this feature:
- Logon to Merchant Site Admin URL (e.g., your domain.com/admin)
- Click on Stores > Configuration > ADVANCED > Admin > Security > Add Secret Key to URLs
- Select YES from the dropdown options
- Save Config
We are stands out with support policy and customer care. Please check our Top Magento Extensions: Amazon Advertising API extension, Free Custom Menu, Slider Manager and other ecommerce extensions.